How to configure Cisco Router on a stick
Posted on 17 March 2013 by Beaming SupportIf you wish to use multiple vlans on your network you will need a layer 3 device to connect these networks.
The device is called a router on a stick and we’re going to show you how to configure Cisco router on a stick in this article.
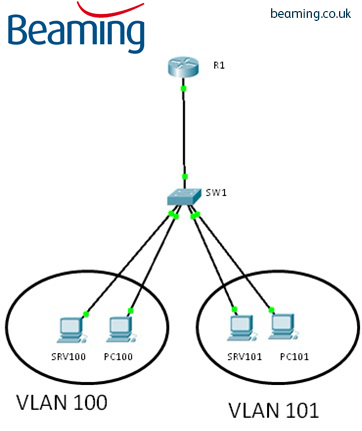
Firstly, please see the topology below:
First we shall create the VLANs:
SW1#configure terminal SW1(config)# vlan100 SW1(config-vlan)# name vlan100 SW1(config-vlan)# exit SW1#configure terminal SW1(config)# vlan101 SW1(config-vlan)# name vlan101 SW1(config-vlan)# exit SW1(config)# interface FastEthernet0/1 SW1(config-if)# switchport mode trunk SW1(config-if)# spanning-tree portfast SW1(config)# interface FastEthernet0/2 SW1(config-if)# switchport access vlan 100 SW1(config)# interface FastEthernet0/3 SW1(config-if)# switchport access vlan 100 SW1(config)# interface FastEthernet0/4 SW1(config-if)# switchport access vlan 101 SW1(config)# interface FastEthernet0/5 SW1(config-if)# switchport access vlan 101
We now need to configure the router:
R1# configure terminal R1(config)# interface FastEthernet0/0.100 R1(config-if)# encapsulation dot1Q 100 R1(config-if)# ip address 192.168.100.254 255.255.255.0 R1(config-if)# exit R1(config)# interface FastEthernet0/0.101 R1(config-if)# encapsulation dot1Q 101 R1(config-if)# ip address 192.168.101.254 255.255.255.0 R1(config-if)#^Z
Once you have assigned the appropriate IP addresses and gateway to the PCs you will be able to communicate between the VLANS. If you wish to limit the traffic that passes between vlans you can assign an access list to prevent unwanted traffic from traversing the VLANs.
In the below example with will permit only http traffic to the SRV100 and SRV101 from the opposing VLANS:
R1(config)#access-list 150 permit tcp any host 192.168.100.1 eq 80 R1(config)#access-list 150 deny ip any any R1(config)#access-list 151 permit tcp any host 192.168.101.1 eq 80 R1(config)#access-list 151 deny ip any any R1(config)#int fast R1(config)#int fastEthernet 0/1.100 R1(config-subif)#ip access-group 151 out R1(config-subif)#int fastEthernet 0/1.101 R1(config-subif)#ip access-group 150 out
We're networking experts
When it comes to private wide area networks and business continuity services, a “set it and leave it” approach just doesn’t cut the mustard.
More guides, straight to your inbox
Our monthly how-to guides, cyber security tips and business tech advice help businesses stay online and make the most of their connectivity.
You have reached the entry limit