Why you need a route map on a NAT statement
Posted on 21 June 2019 by Beaming SupportCisco ISR VPN troubles with 1 to 1 NAT?
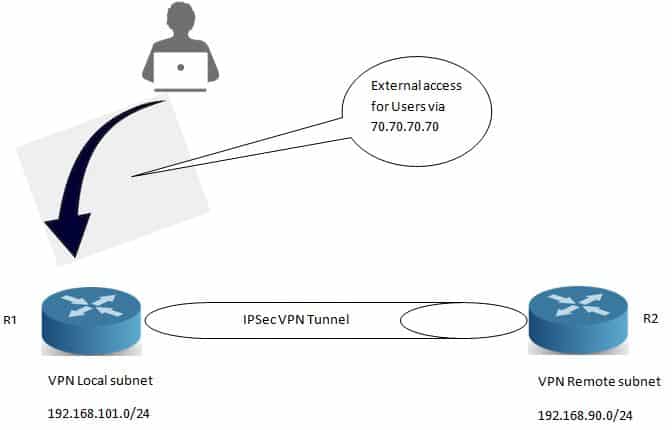
If you have the example NAT configuration on your Cisco ISR and a VPN you will quickly find that VPN traffic to the internal address of your NAT statement is not passing traffic over the VPN. But all other devices within the VPN proposal are passing traffic over the VPN. See below.
Here’s how to configure a site to site VPN
R1 has the below command.
Ip nat inside source static 192.168.101.111 70.70.70.70
With the above command in place you will very quickly realise that host 192.168.101.111 is not able to talk to the remote subnet of 192.168.90.0/24, the reason for this is that it will not hit your default NAT rule as it has been configured as a 1 to 1 NAT, this will then mean that any packet destined for 192.168.90.0/24 will be NAT’ed out to 70.70.70.70. To overcome this we will be using the above NAT statement with a route map to deny the VPN interesting traffic, see the below configuration for R1.
route-map 1to1NO-NAT permit 10
match ip address VPN-TRAFFIC
ip access-list extended VPN-TRAFFIC
10 deny 192.168.101.0 0.0.0.255 192.168.90.0 0.0.0.255
20 permit ip host any any
Now all we need to do is amend our NAT statement, see the below
Ip nat inside source static 192.168.101.111 70.70.70.70 route-map 1to1NO-NAT
After applying the above 192.168.101.111 will be able to communicate with the remote VPN subnet.