Sophos UTM endpoint protection theory
Posted on 5 March 2019 by Beaming SupportIn this article we are going to look primarily at the theory and application of the Web Control feature available for the Sophos UTM Endpoint Protection program installed on client machines via the UTM deployment agent.
What is Web Control?
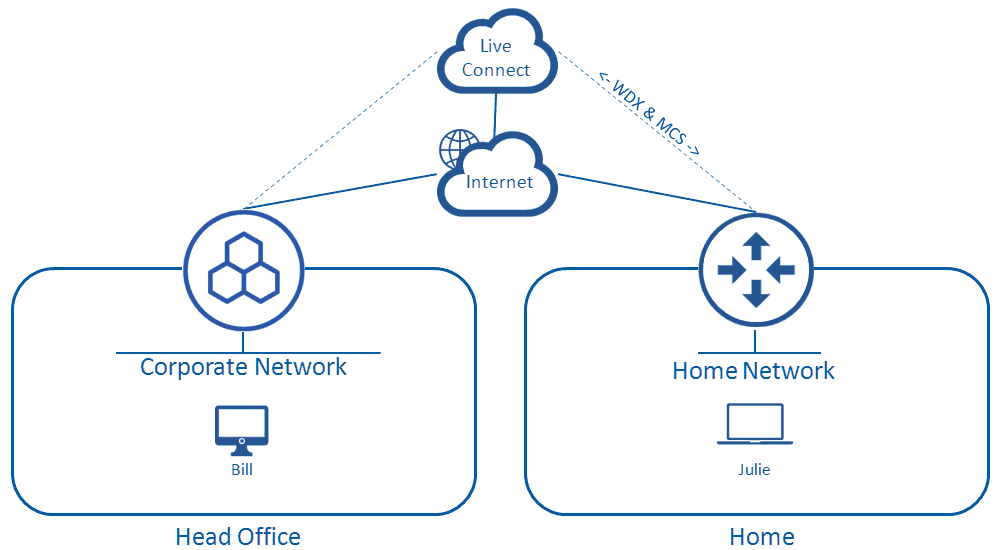
Web Control is a feature of the Endpoint Protection installed on client machines from their organisation’s UTM/s and provides remote web filtering without them needing to be in the office. It does this by storing a local copy of the central UTM web URL filtering policy, so that when a computer is connected to a remote network (like one at home) and not routing traffic through ha UTM appliance, URL filtering rules are still enforced via the Web Control feature.
When in an office with a Sophos UTM, all of your traffic should be filtered by it. It will perform a variety of checks to protect you from most of the threats we are exposed to on the Internet. However, when you take your corporate computer back home you are no longer being protected by a sophisticated next generation firewall, rather your only protection is your home router which does nothing but block incoming traffic, it can’t detect dangerous files that you are downloading or warn you of malicious websites.
That is until your IT Administrators install the Sophos UTM Endpoint Protection on the machine, which will do its best to protect your computer from malware that attempts to infect it. However your corporate polices require that your web access is restricted to the sites that you need, and to block any websites that could cause harm to the machine.
How does Web Control communicate with the UTM?
Before anything you must first have Endpoint Protection (EP) enabled on the UTM, and deploy the agents on the corporate machines.
Once enabled, the UTM does the following to register with LiveConnect:
- UTM connects to LiveConnect to register
- On successful registration a unique ID and certificates are generated and sent to the UTM
- UTM uses certificates to communicate securely with LiveConnect
When installing the Sophos EP from the deployment agent, you will have an install file with the format of SophosMCSEndpoint_<TOKEN>.exe the <TOKEN> is the unique ID used to register the client with LiveConnect.
You can find this file on the UTM, under Endpoint Protection > Computer Management > Deploy Agent
Installation process of the exe file
- It Checks for existing products that are installed on the system
- The installer will then warn about 3rd party products installed.
- It’ll then install MCS
- Next the program will register with LiveConnect and download MCS/AutoUpdate polices
- Install Auto Update then apply the downloaded policy
- Download Sophos AV+Updates then install it.
The Sophos Anti-Virus (SAV) which is embedded within EP uses Management Communication System (MCS) by default to acquire endpoint policies from the UTM such as whether or not it will use anti-virus, tamper protection or device control, along with this information the UTM policies for web filtering are all pulled across. All of this is done over HTTPS.
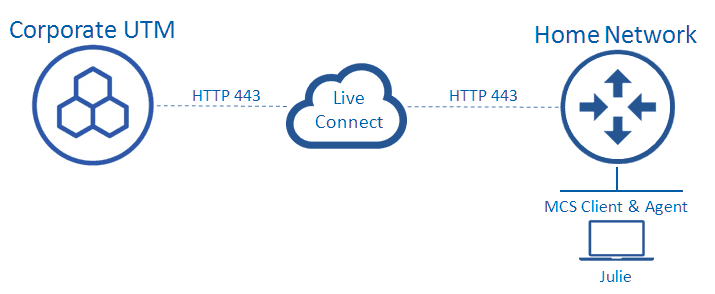
There are two services that are installed by the MCS installer, which are used to check and process information downloaded and stored via LiveConnect.
Sophos MCS Client
This is a service installed on the machine, and is responsible for checking in with LiveConnect periodically in 20 second intervals for new commands via a secure HTTPS connection. An example command is “Fetch New Policy”, and once received it will execute it and download it to “C:\ProgramData\Sophos\Management Communication System\Persist”. This information is then forwarded to the MCS Agent which will use then process the execute command from the client. The final thing the client does is notify LiveConnect of the status of the agent, and removing local cached information that has been successfully actioned.
C:\ProgramData\Sophos\Management Communication System\Endpoint\Logs\MCSClient.log
Sophos MCS Agent
The agent service processes the information received from the client, and uses adapters to apply configurations to the endpoint components. It is also responsible for gathering status information or notifications to send back to the server, this is done by storing it locally so it can be picked up by the MCS client to send to the LiveConnect, which will then be removed once LiveConnect has acknowledged the update.
C:\ProgramData\Sophos\Management Communication System\Endpoint\Logs\MCSAgent.log
The application of Web Control
Proxy Web Profiles – Web Protection > Web Filtering Profiles
To begin the process of setting up endpoint protection, you should create a new web filtering policy that will be used with your web control polices. This is to avoid inconsistent mappings between content filter actions and users/groups. Please note that quotas aren’t applicable in web control and ‘Warn’ is the default option for quotas.
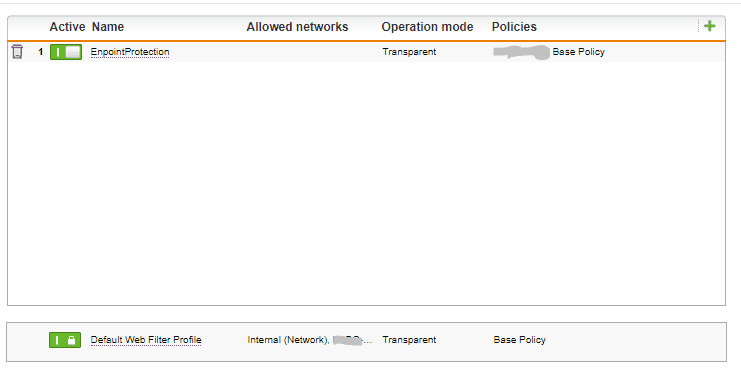
Here you can add the “Default” group to “Allowed endpoint groups” which will enforce all endpoint groups to use this policy first, before using the base policy. This is so that you have control to restrict remote users further.
Endpoint protection Groups – Endpoint Protection > Comptuer management
You can create a custom Endpoint group via the Manage Groups tab, this will allow you to add specific registered endpoint clients so you can control which computers can do what. This allows for further control as you can create a group and apply it to another web filtering policy to grant different access.
Creating Web Filtering Exceptions – Web Protection > Filtering Options
You can create a web policy that includes the group of endpoint users and the list of URLs that you would like them to bypass, if they need to download restricted files or if there was an SSL error.
These polices will be downloaded by the MCS Client, and processed by the MCS Agent so that the web control feature of the program is aware that they can access that link.
End point protection logging
UTM Logs
Logs can be found either by logging into the device via SSH or the Web Admin.
Live Connect Diagnostic Logs
SSH = /var/log/epsecd.log
WebAdmin = Logging & Reporting > View Log Files > Endpoint Protection
Endpoint Browsing Traffic Logs
SSH = /var/log/eplog.log
WebAdmin = Logging & Reporting > View Log Files > Endpoint Web Protection
Data sent to LiveConnect from the UTM |
| 2018:07:26-17:57:33 filter epsecd[5666]: I id=”4233″ severity=”info” sys=”System” sub=”epsecd” name=”Sending data to Sophos LiveConnect to sync UTM Web Policy Changeset“ |
Data sent to endpoints via Liveconnect |
| 2018:07:26-17:56:40 filter epsecd[5666]: I id=”4212″ severity=”info” sys=”System” sub=”epsecd” name=”Acknowledging report(s)” reports=”-1,-1″ |
Data received from endpoints via Liveconnect |
| 2018:07:26-17:57:33 filter epsecd[5666]: I id=”4211″ severity=”info” sys=”System” sub=”epsecd” name=”Received report(s) from Sophos LiveConnect“ |
Endpoint Logs
To enable logging on an endpoint machine, you should add a loglevel tag to the config.xml file found in
C:\ProgramData\Sophos\Management Communication System\Endpoint\Config
<McsClient>
<logLevel>0</logLevel>
</McsClient>
<McsAgent>
<logLevel>0</logLevel>
</McsAgent>
There are actually 6 log levels to choose from which will control how intensive the logging is
0 = Trace
1 = Debug
2 = Information
3 = Warning
4 = Error
5 = Fatal
Conclusion
With all of this information you should hopefully be on your way to better diagnose and understand the weird and wonderful way that the Endpoint Protection application works.
We'll help you protect business data
Found this useful?
Get how-tos from our tech team, cyber security advice and business tips for SMEs in our monthly email bulletin.