Azure AD Connect fails synchronisation after conditional access is enabled.
Posted on 11 September 2023 by Beaming SupportIf you enable conditional access policies and use the default settings, you may find that Azure AD Connector application stops synchronising password changes and Active Directory changes. This is due to the default condition policy which enforces MFA for all users. As the MSOL user that is used by the Azure AD Connect application is a standard Domain User, it will be required to Multifactor Authenticate by the conditional policies, and fail.
By adding the MSOL user account to the ‘Require MFA for Internal users (admins not included) – Basic’ conditional policy, this will resolve the issue and the Azure AD Connect Application will resume synchronising your on-premise AD and passwords.
Logon to the Microsoft Entra Admin Center, https://entra.microsoft.com (formerly Azure Admin Center)
Select ‘Protection’ in the left hand pane and ‘Conditional Access’.
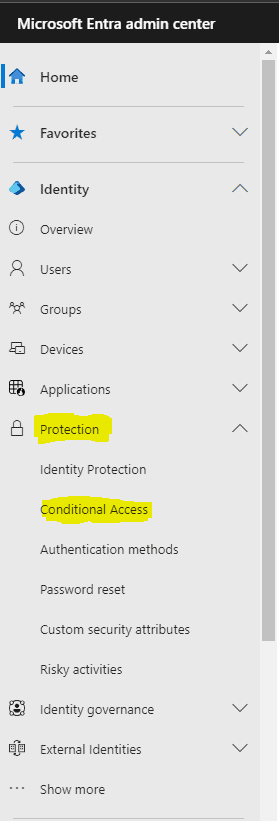
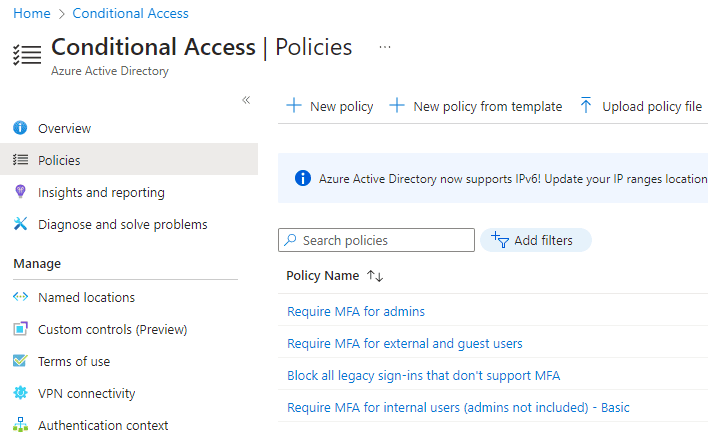
Select ‘Policies’ and in the right hand pane select ‘Require MFA for internal users (admins not included) – Basic’
Under assignments select ‘All users included and specific users excluded’, in the right-hand pane select ‘Exclude’ and add the On-Premises Directory Sync account.
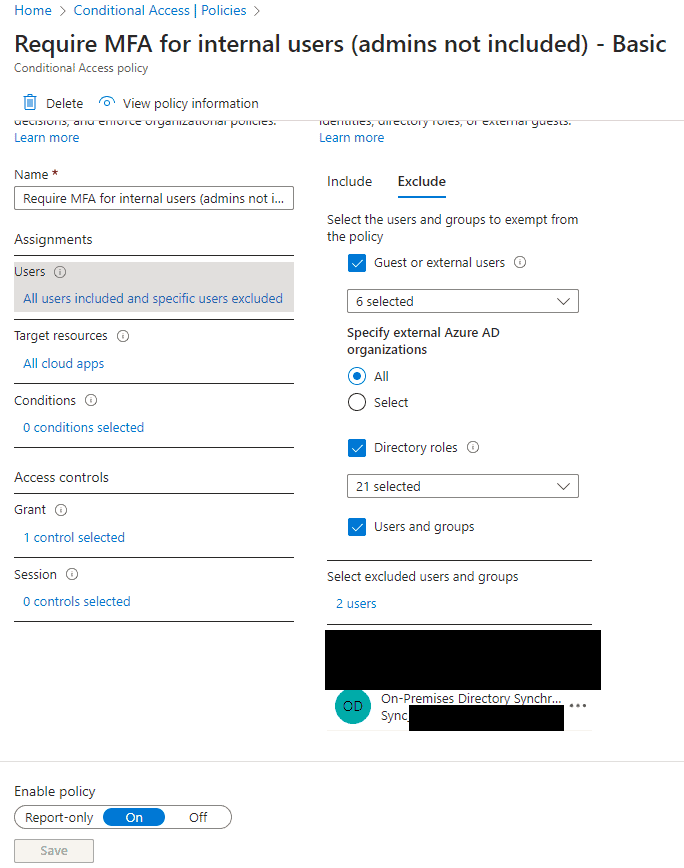
Save the policy.
Restart the Azure AD connector, and check that the synchronisation now passes.
Find more information from our tech experts in our knowledge base:
About Beaming
We’re Beaming, a specialist internet service provider (ISP) for businesses. We’ve been helping organisations across the UK with fast, reliable, and secure voice and data connectivity, as well as managed services, since 2004.
From the resilient and secure network we’ve built, to the choice of tailormade products all supplied with expert service, we provide peace of mind that businesses require.
We know that your business is unique, so we take the time to get to know you and your specific needs. If you’re looking for a reliable ISP for your business, we’d love to chat.