Cyber threat report 2017: Attacks on UK businesses increase to 231,028 each
Attacks on British businesses surge in final quarter to surpass 2016 levels
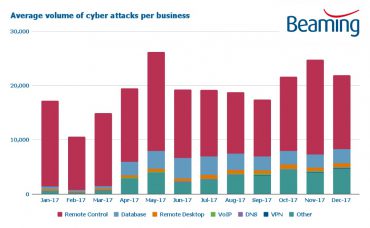
UK businesses were subjected to an average of 231,028 internet-borne cyber attacks in 2017. On average, each UK firm with an internet connection experienced 633 attempts a day to breach their corporate firewalls last year, with more than two-thirds (70 per cent) of attacks targeting connected devices such as building control systems and networked security cameras.
The volume of cyber attacks increased by 24 per cent in the final quarter of the year, with companies – on average – experiencing 68,212 attacks each between October and December. This extra activity at the end of 2017 ensured the number of cyber attacks last year on UK organisations surpassed 2016 levels, when Beaming recorded 228,659 attacks per business.
We also recorded a six-fold surge in attacks targeting company databases, a five-fold increase in attempts to hijack Domain Name Systems and a three-fold rise in efforts to infiltrate remote desktop systems between the first and final quarters of 2017.
Sonia Blizzard, managing director of Beaming, comments: “2017 was the worst year yet for cyber attacks on British businesses, whose IT security systems are under constant pressure from hackers and malicious computer scripts seeking to exploit any vulnerability. With most attacks targeting relatively simple devices connected to the Internet of Things it is possible many companies are already infected and don’t know about it.”
“Keeping anti-virus software up-to-date is a good first step, but it isn’t enough to combat the growing threat. Businesses need to review their network perimeter regularly, monitor corporate systems for unusual activity and restrict access to personal email and file sharing applications in the workplace.
“A unified threat management device or managed firewall service with full perimeter control, risk assessment and threat mitigation is vital for any company that holds confidential data or relies on their IT infrastructure to remain fully operational.”
Need more recent stats?
Get the quarterly cyber threat report before anyone else
Subscribers to our cyber threat report email receive our cyber threat report first and with exclusive content. Sign up below.