UK businesses targeted 65,000 times each by hackers in three months to June 2017
Increase in cyber attacks sees average number of attacks per business rise to 65,000 over three month period, with a substantial increase in attempts to control company databases
There was an increase in cyber attacks targeting UK-based businesses of more than 50% in the second quarter of 2017, according to a new report from Beaming, the business ISP. Firms were, on average, subjected to almost 65,000 internet-borne cyber attacks each in the three months to June, an increase of 52 percent on the first quarter of 2017.
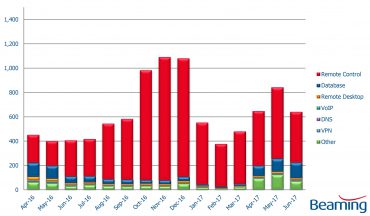
While two thirds (68 percent) of attacks hitting corporate firewalls targeted connected devices such as networked security cameras and building control systems, there was a substantial increase in cyber attacks on company databases. On average, each UK business experienced 105 attempts to take control of their database applications per day in the second quarter of 2017, compared to just 14 in the first three months of the year.
Graph: Cyber attacks per business per day
Sonia Blizzard, managing director of Beaming, comments: “Major organisations have been brought to their knees to by global cyber attacks and our research shows the likes of Wannacry are just the tip of the iceberg. UK businesses were targeted more than 700 times each on a daily basis by hackers over the last three months, who focused on hijacking connected devices and databases.”
“The majority of internet-borne cyber attacks are automated computer scripts that search the web for weaknesses and attack company firewalls for vulnerabilities constantly. Businesses need to keep these vital defences up-to-date, prioritise security over convenience and ensure employees understand both the evolving threat and their cyber security responsibilities.”
Need more recent stats?
Get the quarterly cyber threat report before anyone else
Subscribers to our cyber threat report email receive our cyber threat report first and with exclusive content. Sign up below.